Postdoctoral Scholar yshoukry@eecs.berkeley.edu EECS, University of California, Berkeley, EE, University of California, Los Angeles, ESE, University of Pennsylvania
I am joining the Electrical and Computer Engineering Deaprtment at UMD in Fall 2017 as an assistant professor. I am looking for bright PhD students with interests and expertise in cyber-physical systems, formal methods, control theory, and machine learning!
I am a postdoctoral scholar at UC Berkeley/UCLA/UPenn. I work with Prof. George J. Pappas (UPenn), Prof. Sanjit A. Seshia (UC Berkeley), and Prof. Paulo Tabuada (UCLA). I received my Ph.D. in Electrical Engineering from UCLA in 2015, where I worked with both Prof. Paulo Tabuada and Prof. Mani Srivastava. My main research interests lie in the general area of designing and implementing cyber-physical systems (CPS) and Internet of Things (IoT) with specific interest on security and privacy problems. My research draws on tools from both electrical engineering (e.g. control theory and optimization theory) and computer science (e.g. embedded systems and formal methods). I enjoy building new hardware artifacts, devise new algorithms that work well in practice as well as analyzing their performance from a theoretical point of view.
Menu:
Research Interests
The increasingly tight coupling of cyber (computing/communication) and physical (sensing/actuation) components has opened the door to the development of complex engineered systems. These systems (commonly termed Cyber-Physical Systems, or CPS for short) have enabled a multitude of applications (such as smart power grids, self-driving cars, tele-health, and smart cities). However, as we enter the era of IoT and stand on the edge of an explosion of data generated by these interconnected devices, there has been a corresponding increase in attacks targeting the integrity and security of these systems. These attacks pose a significant threat to often sensitive devices, potentially impairing our relation with these technologies. My approach to addressing these challenges bridges state-of-the-art EE and CS concepts and draws on tools from control and optimization theory, embedded systems and formal methods. My work spans both theoretical and experimental aspects of CPS security and privacy.
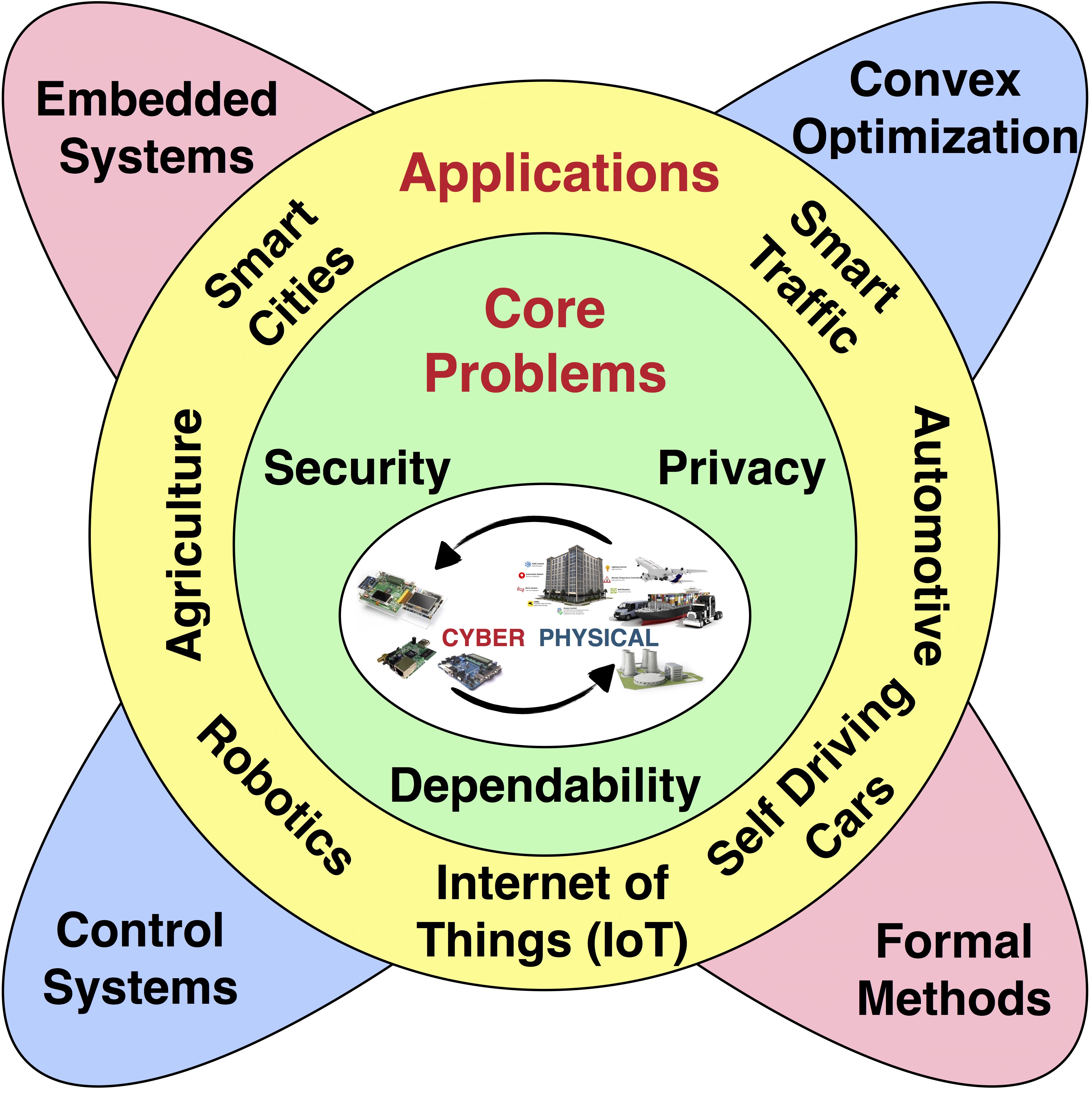
Attack-Resilient Cyber-Physical Systems
The rapidly increasing dependence on CPS in building critical infrastructures—in the context of smart cities, power grids, medical devices, and unmanned vehicles—will open the gates to increasingly sophisticated and harmful attacks with financial, societal, criminal or political effects. While a traditional cyber-attack may leak credit-card or other personal sensitive information, a cyber-physical-attack can lead to a loss of control in nuclear reactors, gas turbines, the power grid, transportation networks, and other critical infrastructure, placing the Nation’s security, economy, and public safety at risk. This motivates the following questions:
- To what extent an attacker can influence the behavior of a CPS? How fatal are such attacks?
- Can traditional cyber-secruity countermeasures be used to detect and mitigte attacks on CPS?
- How to develop a holistic approach to design resilient CPS?
Sensor Spoofing Attacks:
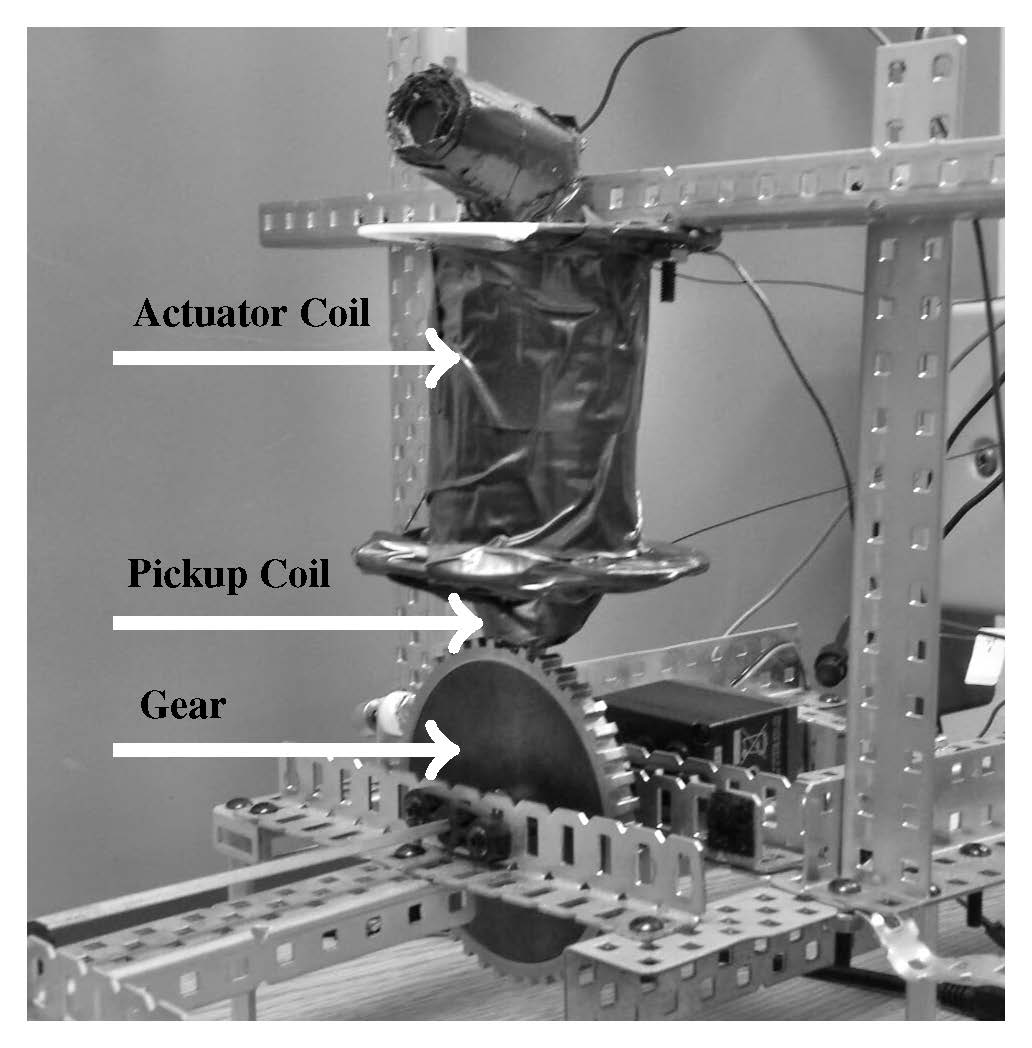
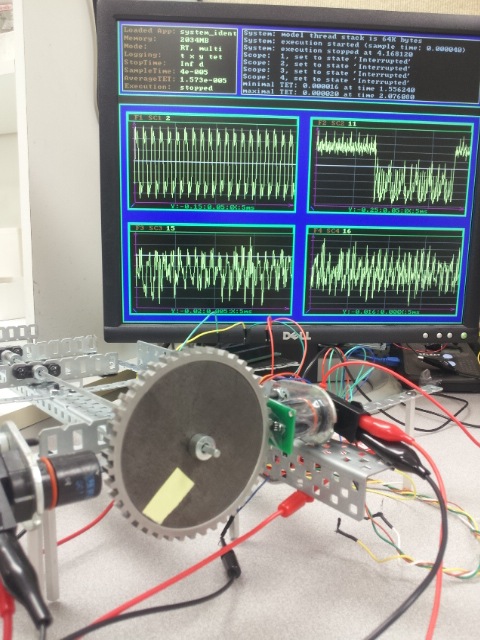 Our work exposes a largely unexplored vector of physical-layer attacks with demonstrated consequences in automobiles. By modifying the physical environment around analog sensors, an attacker can exploit weaknesses in automotive speed sensors in order to corrupt speed measurements and cause life-threatening situations. In particular, we designed and implemented a hardware module, named ABS HACKER (shown in Figure 1), which spoofs the magnetic field sensors used to control Anti-lock Brake Systems (ABS). By placing a thin electromagnetic actuator near the ABS wheel speed sensors, we demonstrated how an attacker could spoof the wheel speed sensors by injecting a magnetic field that replaces the true signal with a malicious one. The mounted attack is of a non-invasive nature, requiring no tampering with ABS hardware and making it harder for failure and/or intrusion detection mechanisms to detect the existence of such an attack. We evaluated the proposed ABS spoofer module using ABS sensors and wheel speed decoders from a real vehicle. Experiments show that, due to the attack, actions taken by the ABS controller can force the driver to lose control over the vehicle.
Our work exposes a largely unexplored vector of physical-layer attacks with demonstrated consequences in automobiles. By modifying the physical environment around analog sensors, an attacker can exploit weaknesses in automotive speed sensors in order to corrupt speed measurements and cause life-threatening situations. In particular, we designed and implemented a hardware module, named ABS HACKER (shown in Figure 1), which spoofs the magnetic field sensors used to control Anti-lock Brake Systems (ABS). By placing a thin electromagnetic actuator near the ABS wheel speed sensors, we demonstrated how an attacker could spoof the wheel speed sensors by injecting a magnetic field that replaces the true signal with a malicious one. The mounted attack is of a non-invasive nature, requiring no tampering with ABS hardware and making it harder for failure and/or intrusion detection mechanisms to detect the existence of such an attack. We evaluated the proposed ABS spoofer module using ABS sensors and wheel speed decoders from a real vehicle. Experiments show that, due to the attack, actions taken by the ABS controller can force the driver to lose control over the vehicle.
Secure State Estimation using Satisfiability Modulo Convex Optimization:
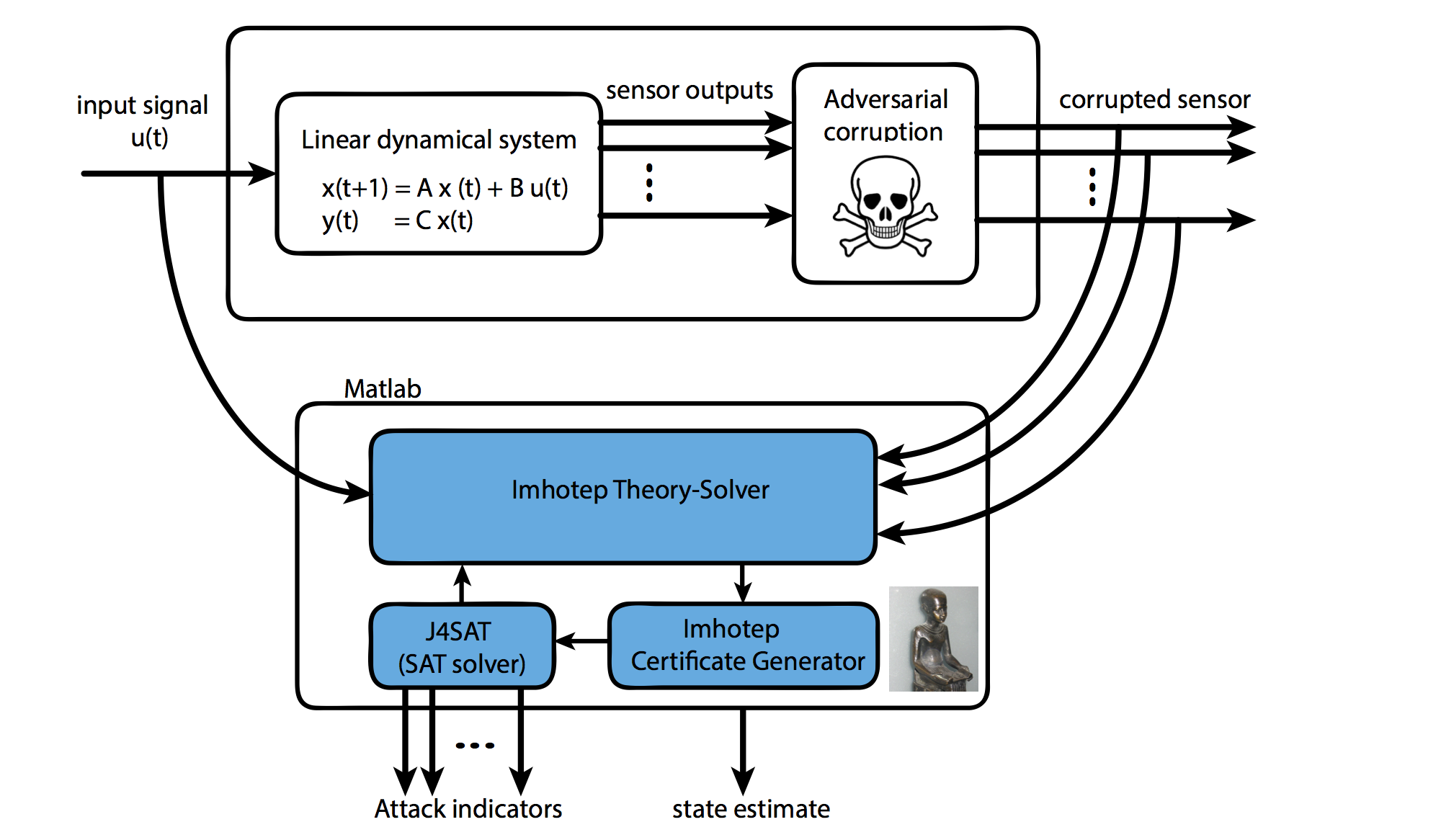 In this work, we focus on scenarios where measurements from various sensors are sent to a central unit to be fused together in order to detect and isolate malicious sensors. Once the malicious sensors are detected and isolated, one can estimate the state of the underlying physical system by using the data collected from the attack-free sensors. This technique is referred to as secure state estimation. Detecting and mitigating attacks on sensory data are NP-hard problem which has been addressed either by brute force search (suffering from scalability issues) or via convex relaxations using algorithms that can terminate in polynomial time but are not necessarily sound.
In this work, we focus on scenarios where measurements from various sensors are sent to a central unit to be fused together in order to detect and isolate malicious sensors. Once the malicious sensors are detected and isolated, one can estimate the state of the underlying physical system by using the data collected from the attack-free sensors. This technique is referred to as secure state estimation. Detecting and mitigating attacks on sensory data are NP-hard problem which has been addressed either by brute force search (suffering from scalability issues) or via convex relaxations using algorithms that can terminate in polynomial time but are not necessarily sound.
To address the challenge of developing a sound and complete algorithm that can efficiently handle the combinatorial complexity of the state estimation problem, our work leverages techniques from formal methods. We showed that the state estimation problem can be casted as a satisfiability problem that includes both logical constraints on Boolean variables as well as convex constraints on real variables. The Boolean variables model the presence (or absence) of an attack, while the convex constraints capture properties of the system state. Towards this goal, We developed IMHOTEP-SMT, a Satisfiability Modulo Theory (SMT)-like solver which is specifically adapted to convex constraint solving, to provide both the attacked sensors and the state estimate. To improve the execution time of the decision procedure, IMHOTEP-SMT is equipped with algorithms that can exploit the underlying geometry of the state estimation problem. The work of IMHOTEP-SMT has been extended into different directions as follows:
- Optimal guarantees in presence of noise: To handle the general case including sensor noise and plant uncertainty, IMHOTEP-SMT solver is augmented with a bank of Kalman filters operating over information collected from subsets of sensors. This novel state estimator is shown to be optimal in terms of mean square estimation error in the presence of adversarial attacks.
- Large-scale systems: The complexity of CPSs is arguably the hardest challenge for the deployment of resilient and secure designs. This is exacerbated by the “trillion devices” scenario posed by the Internet of Things. Devising scalable algorithmic solutions to secure CPS design is, therefore, highly desirable. Therefore, to handle large-scale systems, we proposed a novel multi-modal Luenberger (MML) observer that augments IMHOTEP-SMT solver to further improves its scalability while addressing both memory and runtime efficiency and hence suits the deployment of large scale systems with hundreds or thousands of sensors. This work received the best paper award in ICCPS 2016.
- Nonlinear systems: IMHOTEP-SMT is extended to a class of nonlinear systems known as differentially flat systems. Differentially flat systems are a rich class encompassing various robotic examples. In particular, the effectiveness of the nonlinear version of IMHOTEP-SMT was shown using an unmanned quadrotor performing waypoint navigation while experiencing sensor-level attacks.
Sensor Level Resiliency Against Integrity Attacks:
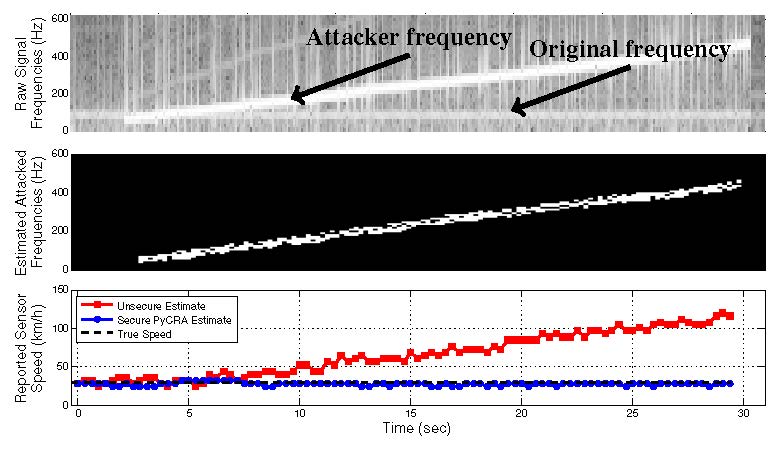
 Unlike secure state estimation which can be considered as a system-level defense mechanism, I introduced PyCRA; a Physical Challenge-Response Authentication scheme which can be seen as a sensor-level security scheme. In traditional challengeresponse authentication schemes, one party requires another party to prove its trustworthiness by correctly answering a question or challenge. This challenge-response pair could be a simple password query, a random challenge to a known hash function, or other similar mechanisms. Unlike traditional challenge-response authentication, the challenge introduced by PyCRA comes in the form of a physical stimulus placed on the environment by an active sensor. The proposed physical challenge operates in the analog domain and is designed so that an adversary cannot issue the correct response because of immutable physical constraints rather than computational or combinatorial challenges. In particular, PyCRA provides security for active sensors by continually challenging the surrounding environment via random but deliberate physical probes. PyCRA provides an authentication mechanism by analyzing the responses to these physical probes against precise mathematical models and ensuring that the underlying physics involved are not violated. By leveraging techniques from estimation theory and signal processing, I was able to design PyCRA so that it does not only detects malicious attacks, but also provides resilience against them. The effectiveness of PyCRA is demonstrated in detecting and mitigating attacks through several case studies using two sensing systems: (1) magnetic sensors like those found on gear and wheel speed sensors in robotics and automotives, and (2) commercial Radio Frequency Identification (RFID) tags used in many security-critical applications.
Unlike secure state estimation which can be considered as a system-level defense mechanism, I introduced PyCRA; a Physical Challenge-Response Authentication scheme which can be seen as a sensor-level security scheme. In traditional challengeresponse authentication schemes, one party requires another party to prove its trustworthiness by correctly answering a question or challenge. This challenge-response pair could be a simple password query, a random challenge to a known hash function, or other similar mechanisms. Unlike traditional challenge-response authentication, the challenge introduced by PyCRA comes in the form of a physical stimulus placed on the environment by an active sensor. The proposed physical challenge operates in the analog domain and is designed so that an adversary cannot issue the correct response because of immutable physical constraints rather than computational or combinatorial challenges. In particular, PyCRA provides security for active sensors by continually challenging the surrounding environment via random but deliberate physical probes. PyCRA provides an authentication mechanism by analyzing the responses to these physical probes against precise mathematical models and ensuring that the underlying physics involved are not violated. By leveraging techniques from estimation theory and signal processing, I was able to design PyCRA so that it does not only detects malicious attacks, but also provides resilience against them. The effectiveness of PyCRA is demonstrated in detecting and mitigating attacks through several case studies using two sensing systems: (1) magnetic sensors like those found on gear and wheel speed sensors in robotics and automotives, and (2) commercial Radio Frequency Identification (RFID) tags used in many security-critical applications.
Privacy-Aware Control of IoT
As cyber-physical technology permeates every corner of our lives today, a large amount of sensory data is collected, fused, and then used to orchestrate these systems. Unfortunately, this collected sensor information can have severe privacy implications. This motivates the need for building practical systems that perform sensor fusion on encrypted sensory data. One yet unexplored method of preserving the privacy of sensor data is to encrypt all sensory data before its transmission to a central controller. This would require the control software to perform all necessary calculations over encrypted data, and consequently the resulting actuation signal itself would be encrypted as well. Such techniques can be found in the literature on Secure Function Evaluation (SFE) which include techniques like homomorphic cryptography, Multi-Party Computation schemes including garbled circuits, secret sharing, and others.
On the one hand, a straightforward solution is to implement existing signal processing and control algorithms–as they are–using one or more of these cryptographic primitives resulting in inadequately high execution times and/or enormous amounts of exchanged communication packets between sensors and the central controller hindering the practical use of such techniques. On the other hand, SFE techniques like Partially Homomorphic Encryption (PHE), for example, have matured in recent years to a point where they can be carried out with much greater efficiency. Unfortunately, current advanced control algorithms have not been designed with privacy in mind and hence they cannot be implemented just using computationally efficient techniques like PHE. For that end, we focused on the following instances of this problem:
- Cloud Based Quadratic optimization using PHE: we consider a problem where multiple agents are interested in jointly solving a quadratic optimization problem subject to linear inequality constraints in a privacy-preserving manner. Several variables of the objective function as well as the constraints are privacy-sensitive and owned by different agents. We propose a privacy-preserving protocol based on partially homomorphic encryption where each agent encrypts its own information before sending it to an untrusted cloud computing infrastructure. The cloud applies a gradient descent type algorithm on the encrypted data without the ability to decrypt it. The privacy of the proposed protocol against coalitions of colluding agents is analyzed using the cryptography notion of zero knowledge proofs.
- Privacy-Aware Localization: we focus on re-formalizing sensor fusion algorithms in a way that allows for the use of additive homomorphic encryption that is time-efficient. This opens the door for structuring the localization problem to enable efficient and accurate computation of a target’s location without requiring sensors to make public their locations or measurements.
SOCIUS: Socially Responsible Smart Cities
Every year, 3.5 million people in the US experience homelessness, and 1 in 30 children becoming homeless [25]. Despite numerous government-sponsored programs and efforts by nonprofit organizations, many homeless people live in abject conditions; for example, according to the the U.S. Conference of Mayors 2013 Status Report on Hunger & Homelessness in 2013, across the surveyed cities 21% of people who need emergency food assistance received none. Exacerbating the situation, private citizens and businesses cannot directly distribute food themselves because of practical issues such as complaints from neighboring businesses and perceived risks to themselves. Furthermore, 31 cities in the US have tried (some successfully) to pass legislation against giving food to people in need in public spaces. Rethinking smart city technologies to best serve these people will be essential to maximize their access to services. We envision a socially-aware smart city as one that utilizes its cyber-physical infrastructure for better management of services1. In other words, a socially-aware smart city is one that is responsible for monitoring the needs of its citizens and maximizing the social satisfaction of the myriad stakeholders (government, private citizens, NGOs, ...). We argue that by smartly managing the efforts of public services, NGOs and private citizens, a smart city can improve the efficiency of matching the varying and unpredictable supply with those who need it.
Our long vision of socially-aware smart cities is to examine the theoretical foundations of population modeling, the analysis and design of socially-aware, human-centered planning algorithms, and technological advances that emphasize on new secure and privacy-aware sensing modalities and mobile technologies for sensing and delivery of services in a manner that maximizes social welfare of both the people in need as well as the general population. Arguably, this vision is multidisciplinary and involves many research activities from both engineering and social aspects where societal perception of utility, privacy, and security are key challenges in addressing these research problems. Currently, I am serving as the lead PI on a $200,000, collaborative, NSF-EAGER funded project in which we am investigating a single critical facet of this problem: we am testing the hypothesis that by using cyber-physical infrastructure in smart cities and strategically distributing resources, we can achieve a better balance between supply and demand of resources while maximizing social welfare.
Previous Research Projects
Side-Channel Based Code Disassembler
The aim of this project is to use the processor’s aggregate power consumption to reconstruct (or estimate) the sequence of software instructions that is currently running on the embedded processor. This is similar to idea of side-channel differential power analysis attacks in which the processor’s power is used to leak information about the cryptographic key used by the processor. We believe that existing tools in side-channel differential power analysis do not adequately illuminate the potential for information leakage. In our work, we use ideas from control theory and formal methods in order to better model the problem and build better tools to extract information from the power measurements.
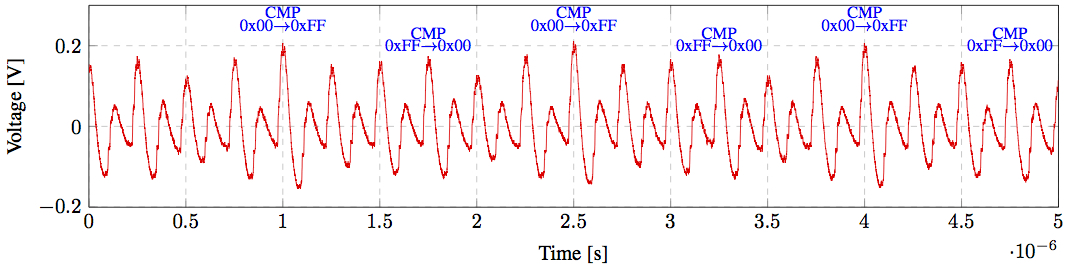 A snapshot of a power trace collected from an ATmega8A processor while alternating between a CMP (complement) and JMP (jump) instruction. The CMP instruction takes only one cycle for execution while the JMP takes two clock cycles. The spike generated depends on the number of bits flipped and the direction of the flip (from zero to one or from one to zero). Initially, the register is loaded with zeros. The first spike corresponds to the negation of all bits from zero to one. The next two spikes corresponds to the JMP cycles. Next all ones in the register are flipped to zeros and a spike is generated. Since the amplitude of the spike differs based on the direction of the flips, the spike generated at this cycle differs from the first spike. Therefore, the same pattern of spikes appears periodically each 2 × (2 + 1) clock cycles. The trace is collected through our side-channel testbed at UCLA’s Networked & Embedded Systems Lab."
A snapshot of a power trace collected from an ATmega8A processor while alternating between a CMP (complement) and JMP (jump) instruction. The CMP instruction takes only one cycle for execution while the JMP takes two clock cycles. The spike generated depends on the number of bits flipped and the direction of the flip (from zero to one or from one to zero). Initially, the register is loaded with zeros. The first spike corresponds to the negation of all bits from zero to one. The next two spikes corresponds to the JMP cycles. Next all ones in the register are flipped to zeros and a spike is generated. Since the amplitude of the spike differs based on the direction of the flips, the spike generated at this cycle differs from the first spike. Therefore, the same pattern of spikes appears periodically each 2 × (2 + 1) clock cycles. The trace is collected through our side-channel testbed at UCLA’s Networked & Embedded Systems Lab."
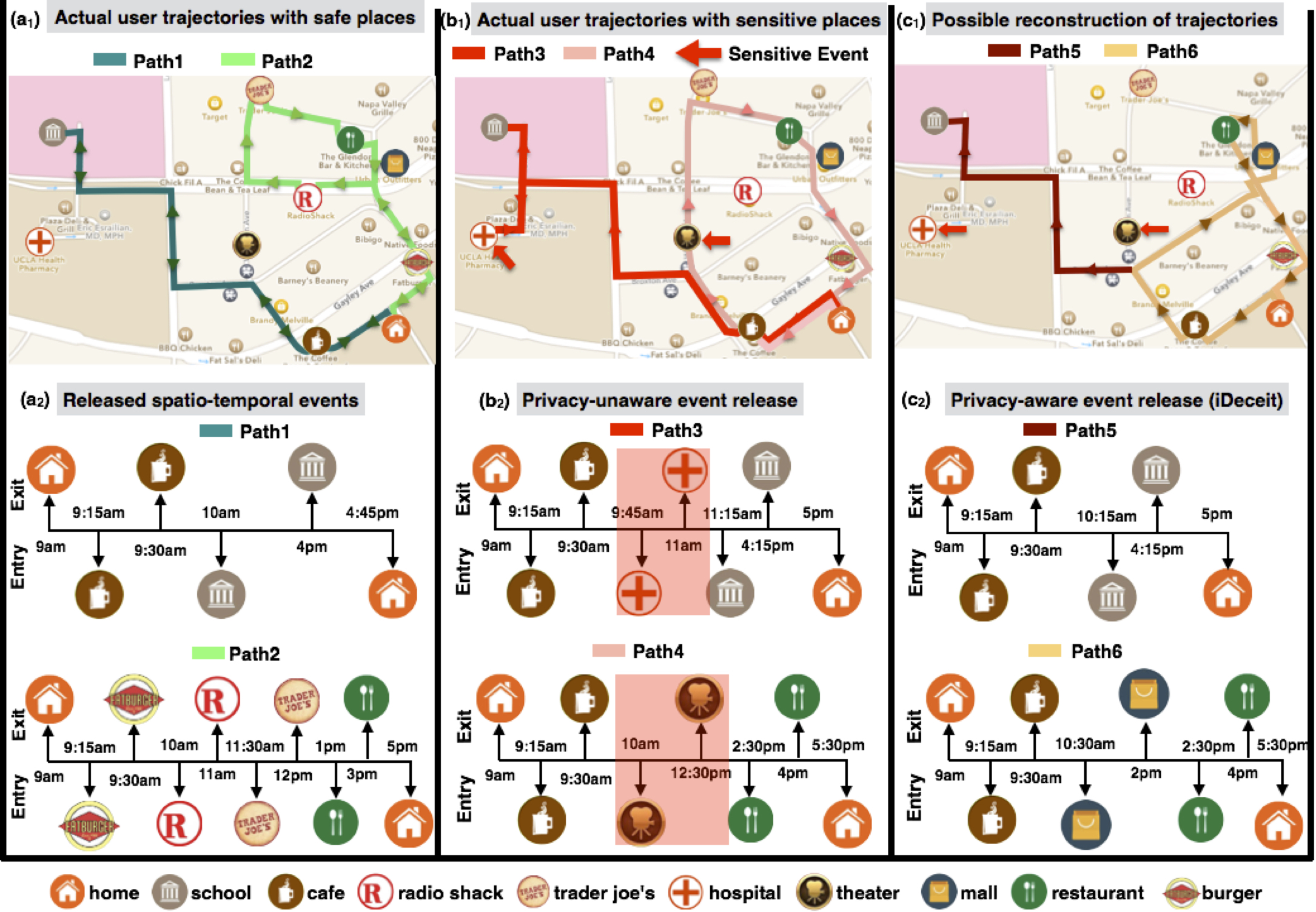
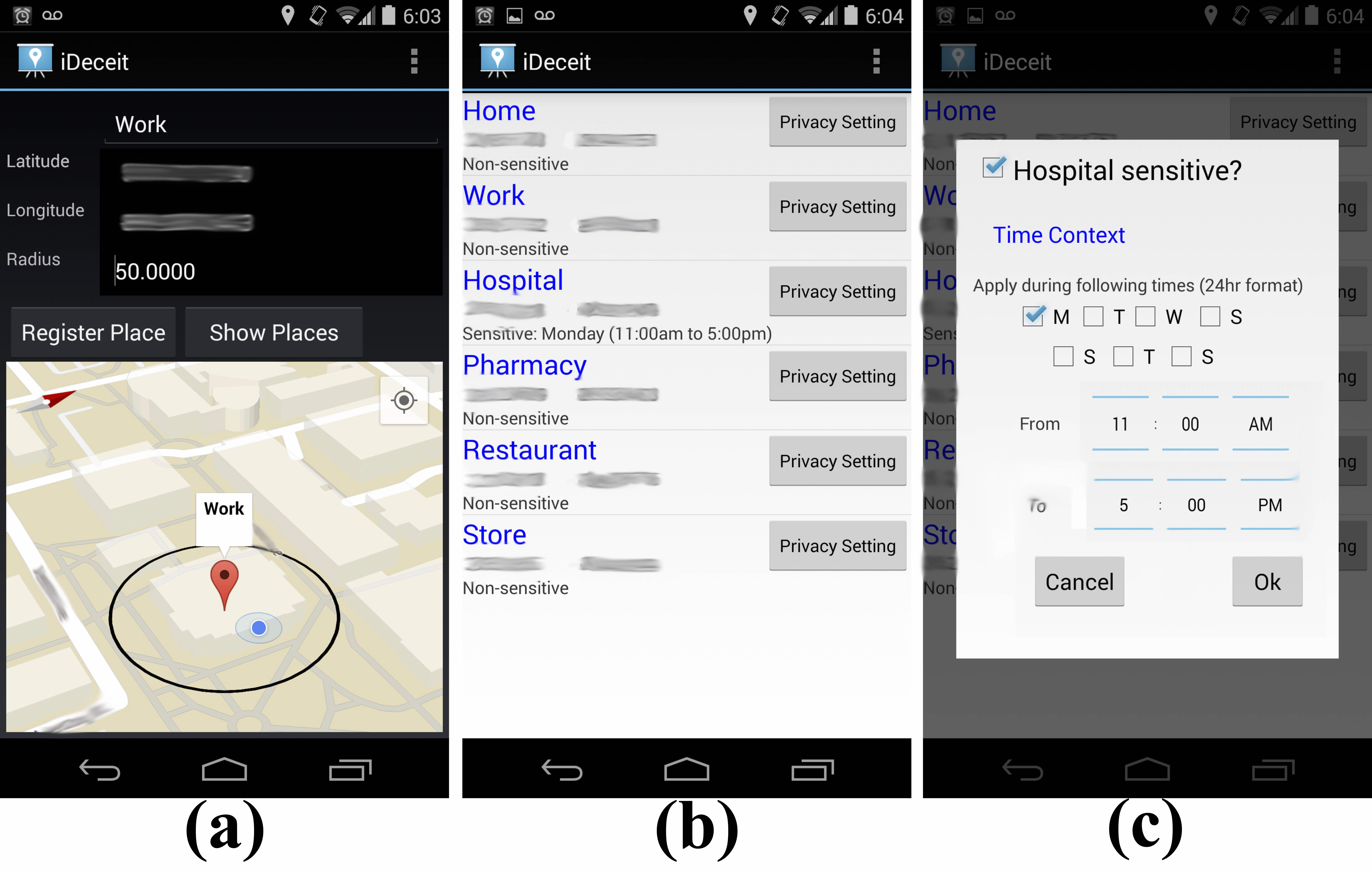
Privacy Firewall for Mobile Phone Location Services
Real-time release of spatio-temporal events on mobile phones while enabling various context-aware and life-logging apps carries significant privacy implications by disclosing, either directly or indirectly, sensitive places that the user has visited. In this project, we aim to develop new "privacy firewall" that protects privacy leaks while mainting the perfromance of the context-aware mobile applications.
Model Predictive Control (MPC)-on-Chip
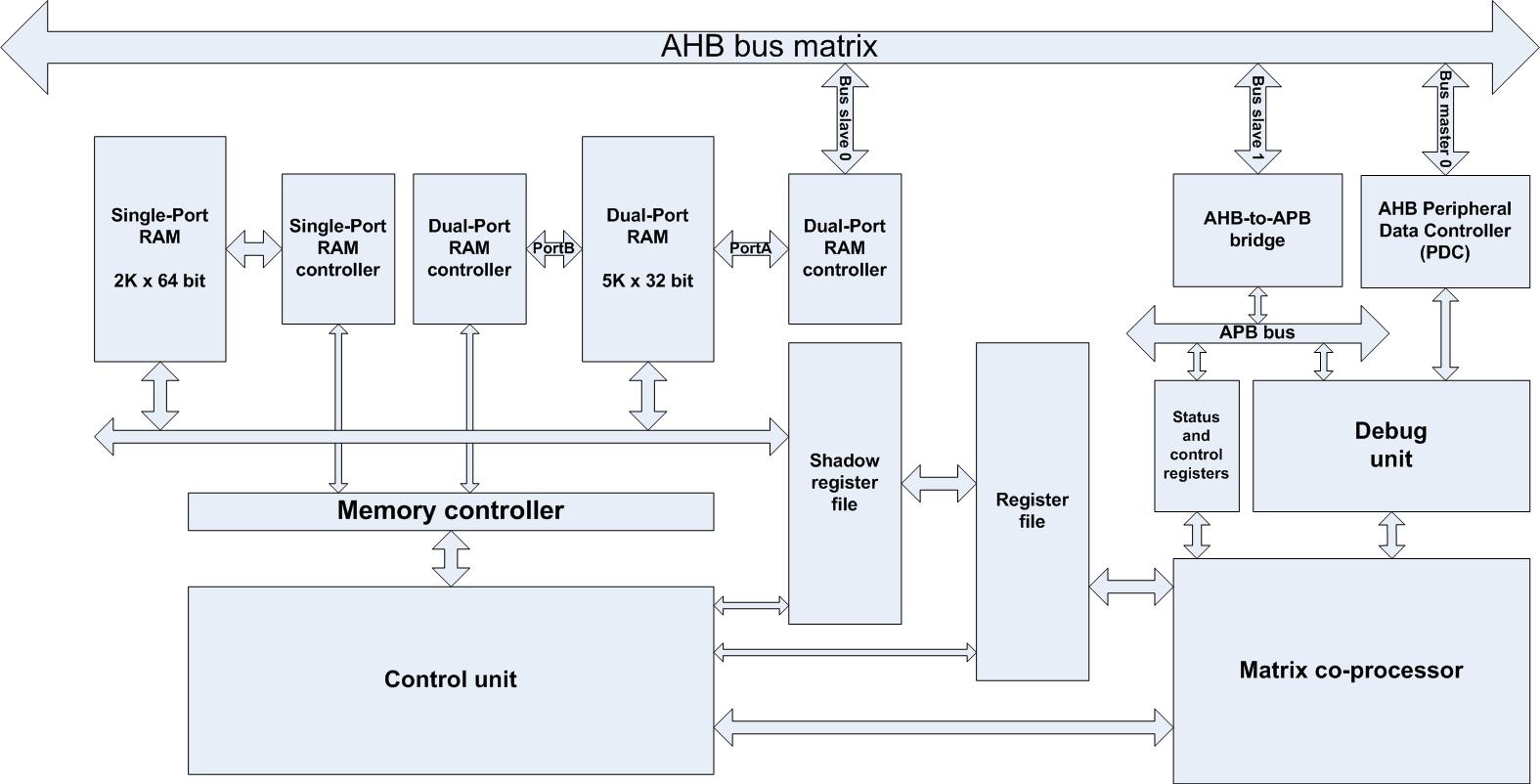
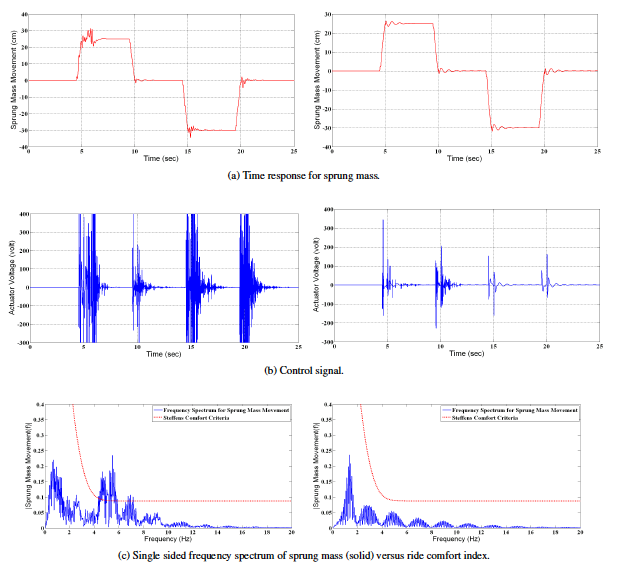
Automotive Active suspensions system is recognized as highly dynamic system with high nonlinearities. Using Adaptive Model Predictive Control adds a new level of implementation complexity on embedded computers due to the required online mathematical optimization. Can we tune a model predictive controller to give acceptable energy consumption while rejecting road disturbance? Can we then obtain an embedded implementation for this controller? First, we tuned and tweaked a Generalized Predictive Controller (GPC) to give acceptable performance while minimizing actuator energy consumption. Second, we provided a co-processor to meet the hard real-time constraints imposed by the solution. The proposed co-processor is then deployed on a CAP9 platform to verify the results. Results obtained show potential further research can be carried out in closing the gap between control and computation.
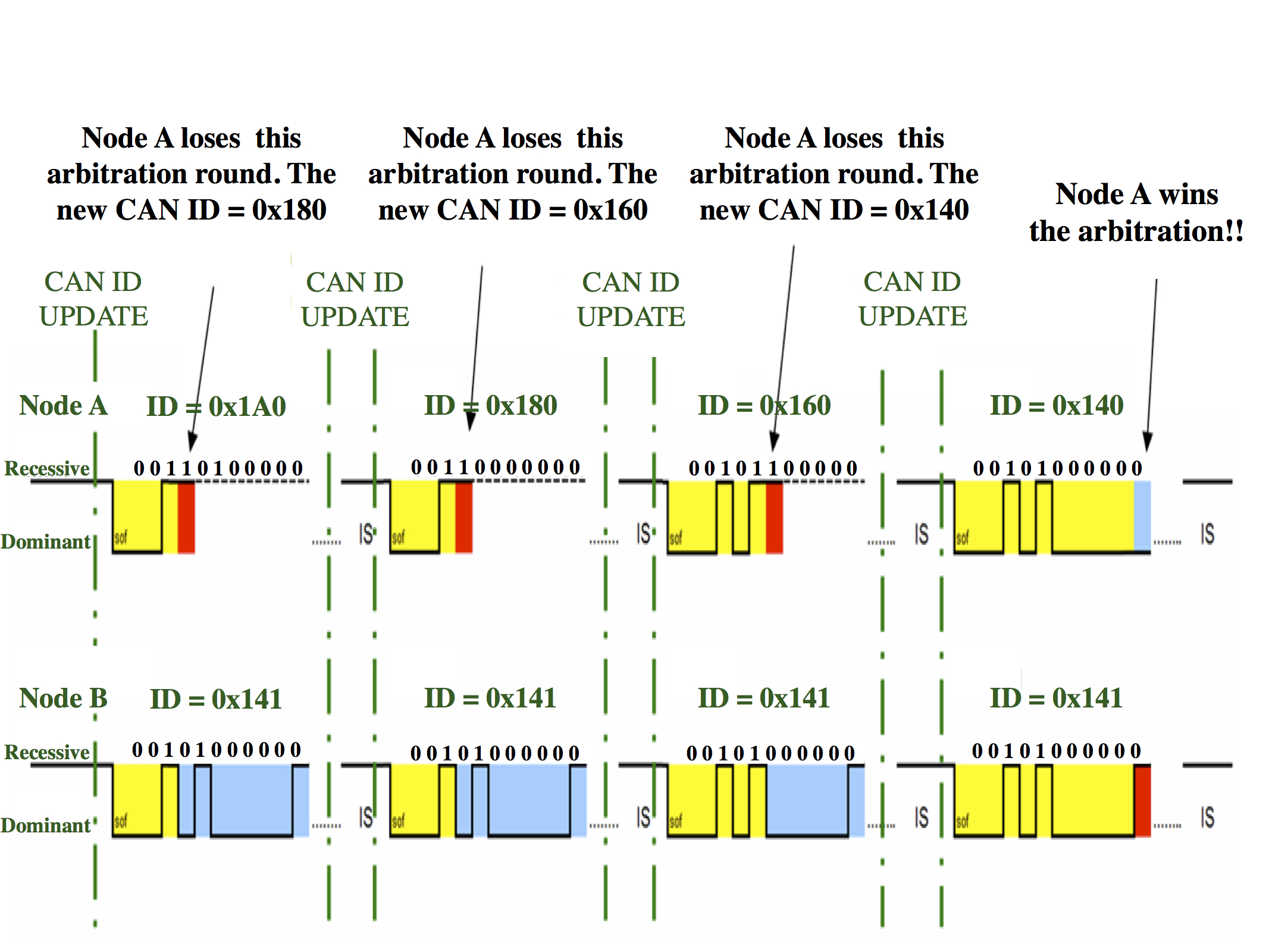
EDF Scheduling of CAN Bus
In this project, we are studying the effect of using Earliest Deadline First scheduling for CAN bus communication and its affect on the behavior of the control loops. Since the EDF algorithm needs to monitor all the CAN traffic to trigger changes in messages priorities, software implementation of EDF can result on a significant overhead in the software. In this project we investigate embedding the EDF scheduling algorithm inside the CAN controller along with its effect on the overall control loop perfromance.